Phishing
Learn About Phishing
What is Phishing?
Phishing is a virtual attack that is done through virtual means of communication. Phishing attacks are attempts at stealing banking information, usernames, passwords, social security numbers, and other sensitive personal data. Often times, cybercriminals include malware in their phishing messages that lets them hack your device. A serious case of phishing leads to identity theft.
Phishing Tips
Phishing emails pose as a serious threat to the privacy of your personal and financial information. Having a plan in place to recognize and respond to phishing scams will keep you safe and protected online. Click on the following tabs to find out some tips on how to identify and avoid phishing.
- Always check the sender's email address carefully and make sure it is from a trusted source.
- Phishing emails often pretend to be from a legitimate organization but the sender's email address might be slightly altered or won't match the organization's name at all.
- Legitimate and trustworthy companies or organizations will never ask for personal information via email.
- Follow with caution when coming across emails trying to evoke emotion from you (urgency, excitement, empathy).
- Phishing emails may contain typos and grammatical errors. Though this is not always the case, it's good practice to spot it when you can.
- Phishing messages may contain attachments that when downloaded will install dangerous malware onto your device. Be cautious of opening any sort of unexpected attachments from unknown sources.
- Phishing emails can enclose links that take you to a spoofed website, engineered to steal information. Get into the habit of hovering over a link before clicking on it, this reveals the real URL in the bottom left of the screen.
- Never enter sensitive information (account logins, credit card numbers, banking info) into websites that are unfamiliar. This could ultimately lead to identity theft.
- Make a habit of spotting the padlock icon in the browser's address bar, to the left of the URL. This indicates that the website is secure and is using Hypertext Transfer Protocol Secure (HTTPS). Browsers without the padlock icon are ran using Hyper Text Transfer Protocol (HTTP), which is not as secure and protected.
- Consider using two-factor authentication by downloading an authenticator app or using an SMS notification to authenticate logins.
- Always keep the computer operating system, malware protection, and web browser up-to-date to make the device less vulnerable to potential hacks.
- Do not reuse the same passwords for multiple accounts and use a personal password key to keep track of your passwords.
- Verify with the sender through an alternative point of contact when receiving an unexpected or suspicious email. Cybercriminals can spoof or hack accounts of people or companies familiar to you and use that to their advantage.
Phishing Examples
Becoming familiar with phishing is a core aspect of digital literacy and is essential in protecting yourself while on the web. Click here to see some frequent examples of phishing received at LACCD.
A clear indicator of a phishing scam is an "urgent" subject line and poor grammar in the email body. Scammers will try to get the sender to reply with a phone number, as seen here, so they can get out of the email system as quickly as possible.
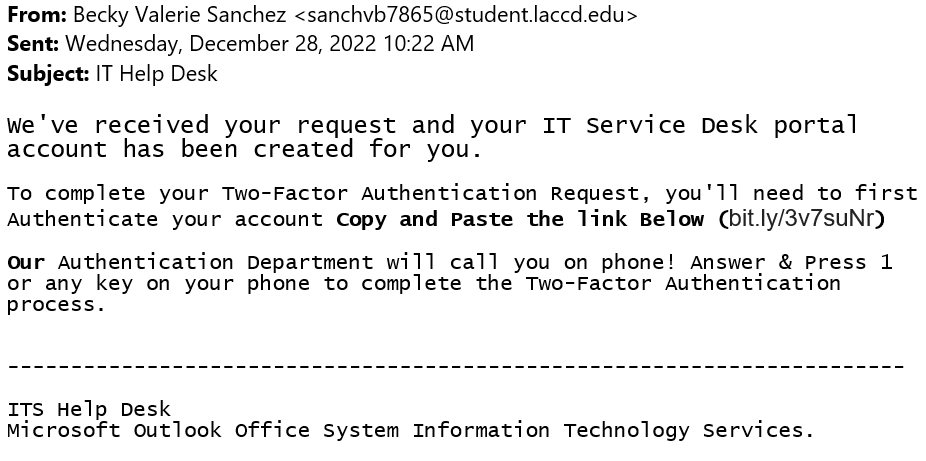
In this example, a hacker took control of a student's LACCD email account and is now using it to pose as an IT Help Desk personnel.
There is a link to "authenticate your account" in the email body. It is good practice to be wary of these kinds of links because they could very much be attempts at stealing account information. Do not open or interact with links from unfamiliar email addresses. Refer to Tip #6 in the Identifying Phishing section.
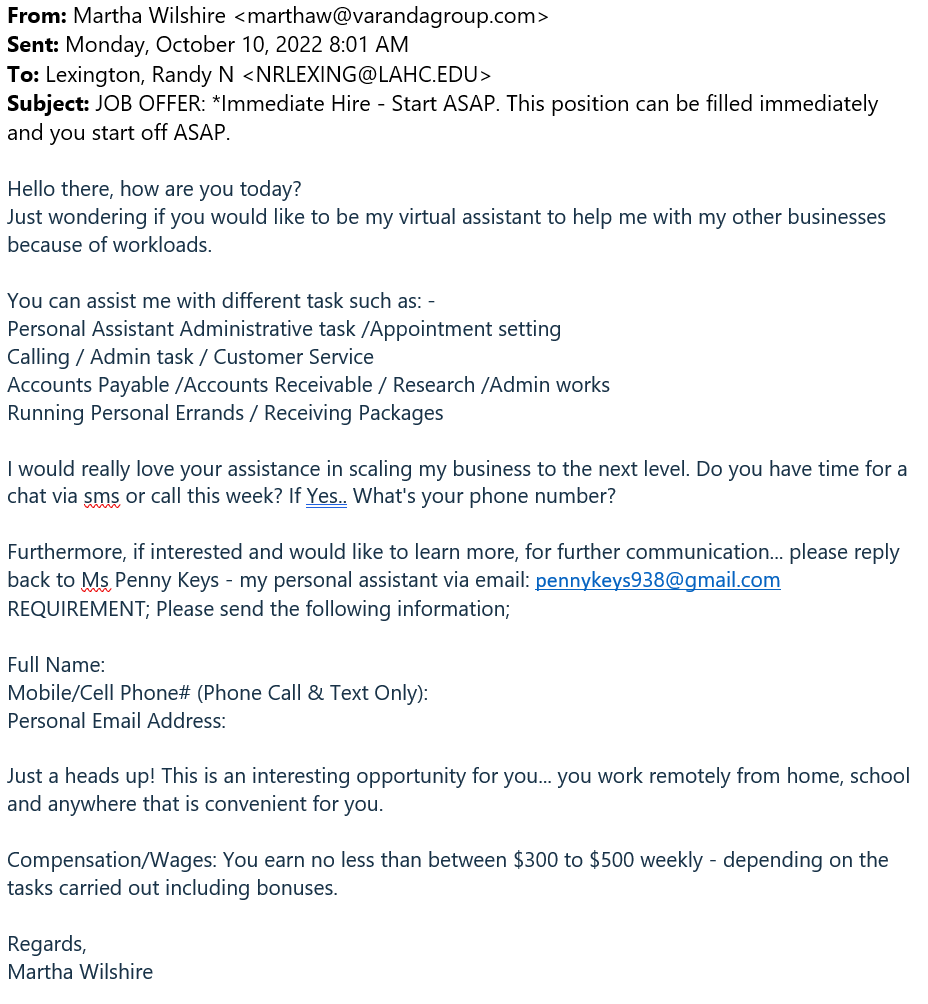
This is an example of a phony job offer email. The sender is asking the recipient to respond to a different email address, claiming that it belongs to their personal assistant. Take it as a red flag whenever an email is instructing the recipient to respond to a different email address.
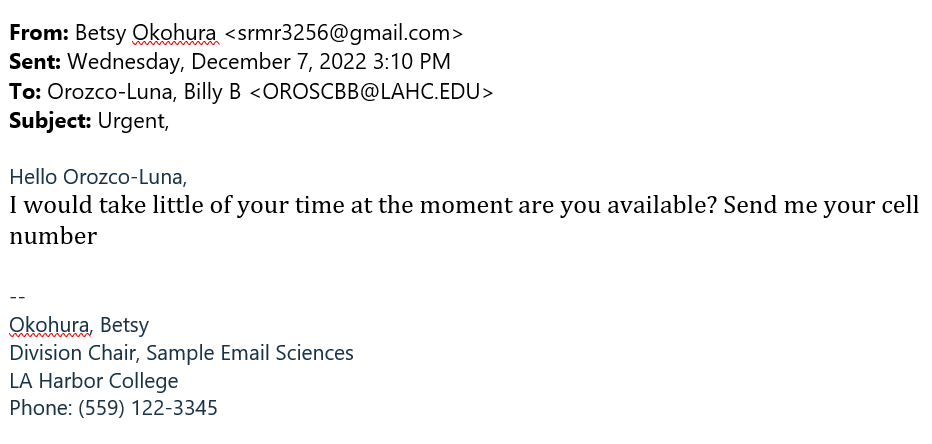
Always be cautious of emails asking for a personal cellphone number. Cybercriminals want a phone number so they can get out of the email messaging system as quickly as possible to carry on with the scam via phone, making it harder for them to be tracked.
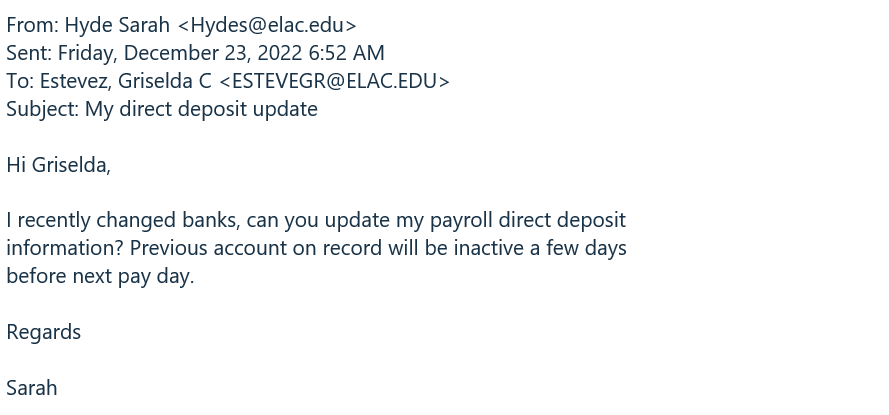
Payroll fraud is when a cybercriminal steals funds from a business through the organization's payroll for their own personal use. It is also clear that the email address is either fake or it is a student email address that has been hacked.
The email includes a proper salutation and outro but, a lack of information in the email's body is a red flag. Scammers will leave information out of emails to prompt the recipient to reply and inquire about more details. Replying to a phishing email is dangerous because it makes you a target for future virtual attacks.
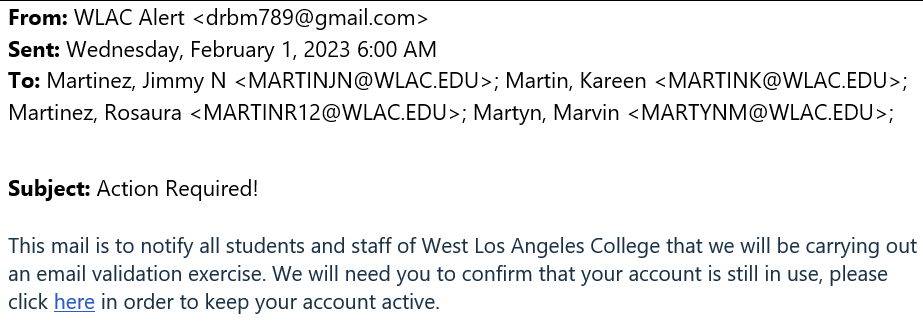
A scammer is posing as an official automated email validation message sent from West Los Angeles Community College. Using a fake link for login portal is a common attempt at stealing any account login information. The scammer retrieves the login info from their fraudulent website to hack into accounts and steal personal information.
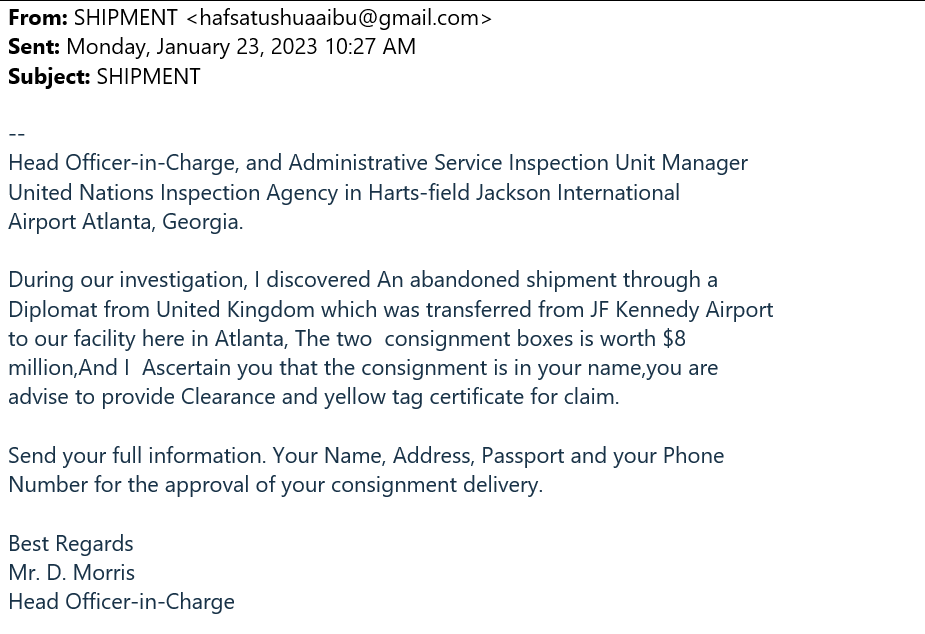
This is poorly structured email claims to be from an official source. The sender is disclosing that they are from an International Airport in Atlanta and explain that there are two boxes in the recipients name worth millions of dollars that need to be picked up. In this case, they are asking for the recipients name, address, passport number, and cellphone number. Scammers ask for passport information to create a fraudulent passport in order to cross borders or take out bank loans in the original passport holder's name.